As our world becomes increasingly digital, the importance of cybersecurity has never been greater. With the rise of cyber threats, protecting data and privacy has become a critical concern for individuals, businesses, and governments alike. This blog examines the future of cybersecurity, the challenges it faces, and the innovative solutions being developed to safeguard our digital lives in this ever-evolving digital age.
Technology assessment in cybersecurity involves evaluating the effectiveness, efficiency, and security of new technologies. This assessment helps organizations understand the potential benefits and risks associated with adopting new cybersecurity solutions.
The Growing Importance of Cybersecurity
In today’s interconnected world, cyber threats are evolving rapidly, posing significant risks to data security and privacy. From financial institutions to healthcare providers, almost every sector is vulnerable to cyber-attacks. The impact of these attacks can be devastating, leading to financial losses, reputational damage, and legal consequences. As such, cybersecurity has become a top priority, with organizations investing heavily in advanced technologies and strategies to protect their digital assets and maintain consumer trust.
Challenges in Cybersecurity
Increasing Sophistication of Cyber Attacks
Cyber-attacks, including phishing, ransomware, and zero-day exploits, are becoming increasingly sophisticated. Organizations need multi-layered security measures to detect and respond to these evolving threats in real-time.
Shortage of Skilled Professionals
The cybersecurity industry faces a shortage of skilled professionals, especially in specialized roles. Addressing this gap requires investment in education and training, as well as leveraging automated tools to augment human efforts.
Rapid Technological Advancements
The swift pace of technological advancements introduces new vulnerabilities for cybercriminals to exploit. Keeping up with these changes is a continuous challenge for organizations, as they must regularly update their security measures to stay ahead of emerging threats in an ever-evolving digital landscape.
Solutions to Cybersecurity Challenges
Encryption
One of the most effective ways to protect data is through encryption. By converting data into a code, encryption ensures that even if information is intercepted, it cannot be read without the decryption key. Advanced encryption methods are essential for securing sensitive data, protecting intellectual property, and ensuring compliance with data protection regulations.
Regular Updates and Patching
Keeping software and systems up to date is crucial in preventing cyber-attacks. Regular updates and patches fix vulnerabilities that could be exploited by hackers. Organizations must adopt a proactive approach to patch management, ensuring that all software, from operating systems to applications, is regularly updated to address emerging threats.
Employee Training
Human error is one of the leading causes of data breaches. Training employees on cybersecurity best practices can significantly reduce the risk of accidental data leaks. Comprehensive training programs should cover topics such as recognizing phishing attempts, using strong passwords, and following secure data handling procedures. Ongoing education helps create a security-conscious culture within the organization.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring multiple forms of verification before granting access to sensitive information. This makes it more difficult for unauthorized users to gain access. Implementing MFA across all systems and applications significantly enhances security by ensuring that even if one authentication factor is compromised, additional layers protect the data.
Technology monitoring involves tracking advancements and trends to ensure up-to-date insights. Signicent supports clients by providing comprehensive analysis and updates on emerging technologies, enabling informed decisions and strategic planning.
Each year Signicent provides consultancy to hundreds of organizations to help transform their innovations to value.
Data Privacy Challenges and Solutions:
Challenges in Data Privacy
Unauthorized Access: Data breaches can result in major financial losses and reputational damage.
Regulatory Navigation: Complying with complicated regulations such as General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) can be difficult and resource intensive.
Vendor Security Risks: Working with third-party vendors can expose enterprises to additional security risks, particularly if these vendors do not follow strict cybersecurity protocols.
Solutions to Data Privacy Challenges
Strong Data Protection Frameworks: Creating comprehensive data protection frameworks ensures secure data management throughout the whole lifecycle, from collection to disposal. Clear policies are required to protect data security.
Continuous Security Monitoring: Regular security checks and vulnerability assessments are critical for discovering and fixing any problems. Continuous monitoring helps to ensure strong security and regulatory compliance.
Effective Vendor Oversight: Ensuring that third-party providers follow strong cybersecurity standards is critical. This entails completing extensive evaluations, regular assessments, and creating unambiguous data protection agreements.
Technology convergence integrates multiple technological advancements, creating new opportunities and efficiencies by combining disparate systems into cohesive, innovative solutions. This synergy enhances functionality and drives industry evolution.
Future Trends in Cybersecurity
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cybersecurity by enabling systems to detect and respond to threats in real-time. These cutting-edge technologies can analyze vast amounts of data to identify patterns and anomalies, helping to prevent attacks before they occur. By continually learning from new data, AI and ML systems become increasingly effective over time, making them indispensable tools in the fight against cybercrime.
Zero Trust Architecture
The traditional perimeter-based security model is becoming obsolete in the face of sophisticated cyber threats. Zero Trust Architecture assumes that threats can come from both inside and outside the network. By verifying every user and device, it ensures that only authorized entities can access sensitive information. This proactive approach minimizes the risk of data breaches and enhances overall security by implementing strict access controls and continuous monitoring.
Blockchain Technology
Blockchain technology offers a secure way to store and share data, making it an ideal solution for enhancing cybersecurity. Its decentralized nature ensures that data cannot be tampered with, providing an additional layer of security. Blockchain’s transparency and immutability make it a powerful tool for securing transactions, protecting intellectual property, and ensuring the integrity of sensitive information.
Quantum Computing
While still in its infancy, quantum computing holds the potential to revolutionize cybersecurity. Quantum encryption could provide unbreakable security, making it impossible for hackers to crack encryption codes. As quantum computing technology advances, it could render current cryptographic methods obsolete, necessitating the development of new, quantum-resistant algorithms to protect data.
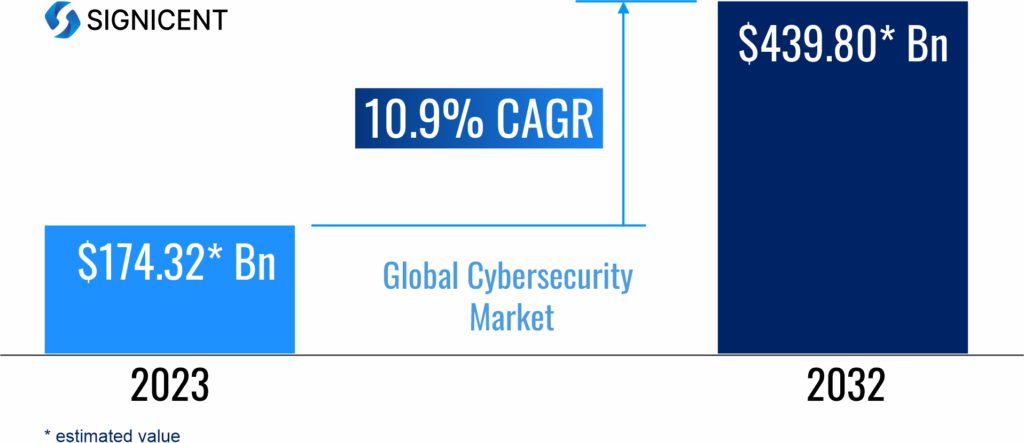
Market Research:
As per Signicent’s Market Researchers, the global Cyber Security market is likely to reach values in the ranges shown below.
Conclusion: The Future of Cybersecurity
As cyber threats continue to evolve, the future of cybersecurity will depend on our ability to innovate and adapt. By leveraging advanced technologies such as AI, blockchain, and quantum computing, we can develop robust security measures to protect data and privacy. However, addressing the challenges requires a collaborative effort between organizations, governments, and individuals. By prioritizing cybersecurity, we can create a safer digital world for everyone, ensuring that our digital lives remain secure, and our data is protected.
Signicent LLP offers comprehensive solutions to address these data privacy challenges. With expertise in technology scouting, market dynamics, and competitive benchmarking, By providing in-depth intellectual property research and continuous monitoring, Signicent ensures that your data protection strategies are effective and up to date, safeguarding your business from potential risks and breaches.
About Signicent LLP
We assist businesses globally in their technology innovations, R&D, new product development, patents, valuation, product commercialization & market research needs.
Services Offered:
- Technology Intelligence
- Market Research
- Patent Landscape
- Technology gap analysis
- Design Patent Search
- Portfolio Analysis
- Freedom to operate
- Bio Sequence Search
- Innovation pipeline identification
- Chemical Structure Search
- Patent Invalidity Search
- Manufacturers Search/ Supplier search
- Patent Licensing Services
Elevate your Innovation and Research with Signicent’s cutting edge approach to assist you with Technology and Market related matters alongside the IP aspect of the analysis.

